Network monitoring is foundational to IT support success, but it’s becoming more difficult as networks grow increasingly diverse and distributed. Spanning a wide range of device types, locations, and users, today’s networks add layers of complexity that put technicians under mounting pressure to deliver reliable connectivity and support at scale.
In response, Domotz is releasing one of our most significant updates yet. This release gives IT teams precise control over who has access, consistent device configuration across environments, clearer visibility into network relationships, and more efficient alerting.
Today we are excited to release the following features at no additional cost:
- Role-Based Access Control
- Device Profiles
- Improved Network Topology
- Alert Dependency for ConnectWise PSA and HaloPSA
What’s new?
Introducing Role-Based Access Control (RBAC)
Tighter access control, improved security, and confidence for IT professionals.
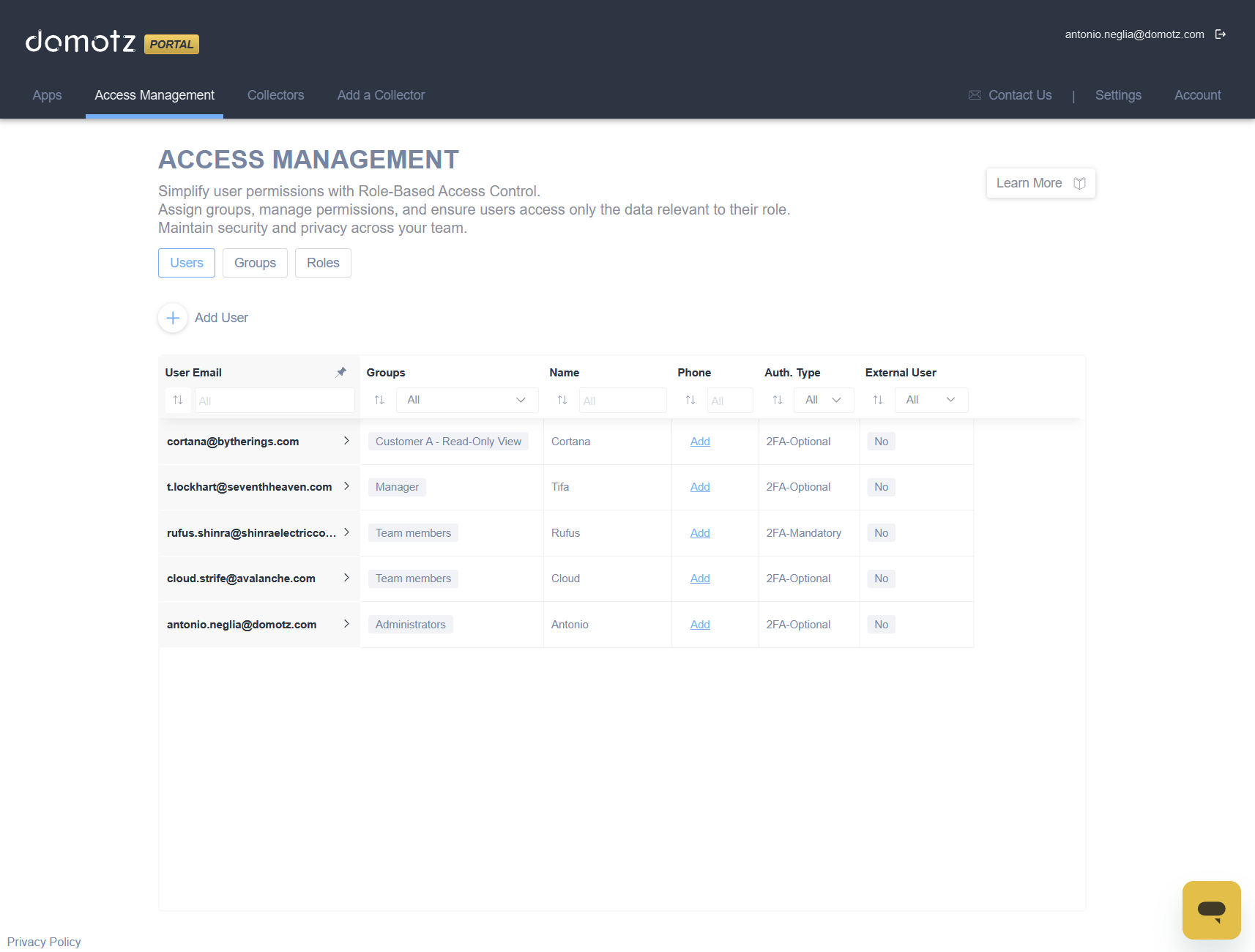
Every IT leader knows the risks of giving the wrong person too much access. One misstep can cause downtime, expose sensitive data, or leave you scrambling during an audit. That’s why RBAC has been one of the most highly requested features and now it’s finally available in Domotz.
We are excited to release Role-Based Access Control (RBAC), a powerful new way to manage user permissions with greater security, confidence, and precision. RBAC ensures the right people have the right access, nothing more and nothing less.
Key Features at a Glance
- Granular Role Definition – Tailor roles with specific permissions (view, edit, manage alerts, etc.) The chart below shows a few examples of what permissions you can assign with RBAC.
- Create Custom Groups – Create a custom group based on your role permissions or select from pre-configured groups to quickly get started with billing-only, read-only access, and more.
- Read-Only Access – Assign Read-Only permissions to provide a user visibility without risk of changes or modifications to devices, configurations, etc.
- Access Transparency – See exactly who has access to what information, anytime.
| Category | Permission (View or Manage) |
|---|---|
| Authorization | Access Management API Keys |
| Global | Add Collectors Delete Collector Cleanup Collector Manage/Unmanage Devices Manage Custom Filters |
| Billing | Billing Details Branding |
| Collector | Collector Configuration VPN Connections Delete Devices Device Management |
| Monitoring Dashboards | Dashboards Page Add New Dashboards Select Dashboards visible to this Role Dashboards Configuration |
| Device Profiles | Device Profiles Apply Device Profiles |
| Alerts Settings | Alerts Settings Page Alert Profiles Contact Channels |
| Integrations Settings | Integrations Tab Scripts Tab |
What Problems RBAC Solves for You
Many IT teams and MSPs struggle with rigid access controls that leave users over-permissioned and exposed to unnecessary risk. Without a way to safely delegate responsibilities across teams, partners, or customers, organizations often find themselves forced into an “all or nothing” approach to permissions. This creates operational risks and compliance headaches.
Be honest, have you ever fallen into one of these buckets?
The “Over-Permissioned Intern”
An intern joins your team and accidentally reboots a critical switch during peak hours. With RBAC, you can assign a “Read-Only” role, letting them observe network and device performance and avoid these types of accidents.
The “Super User/God Mode” for Everyone Policy
All technicians share a full-access account, and one accidentally views another client’s sensitive data. RBAC scopes access to the right clients, sites, or dashboards so boundaries are never crossed.
The “Audit Nightmare”
RBAC gives you the confidence to answer the tough permission-based questions such as “Who has the ability to modify firewall rules on each of our customer sites?”
The Please Hurt Me Plenty “Growing Pains”
Your IT department has doubled in size over the past year. With RBAC, you can ease growing paints by ensuring every new technician and engineer has the right access which saves time and reduces errors.
These are the everyday challenges RBAC in Domotz solves. It’s not just about security, it’s about giving your teams the confidence to work faster, safer, and smarter when working with clients’ or your own networks.
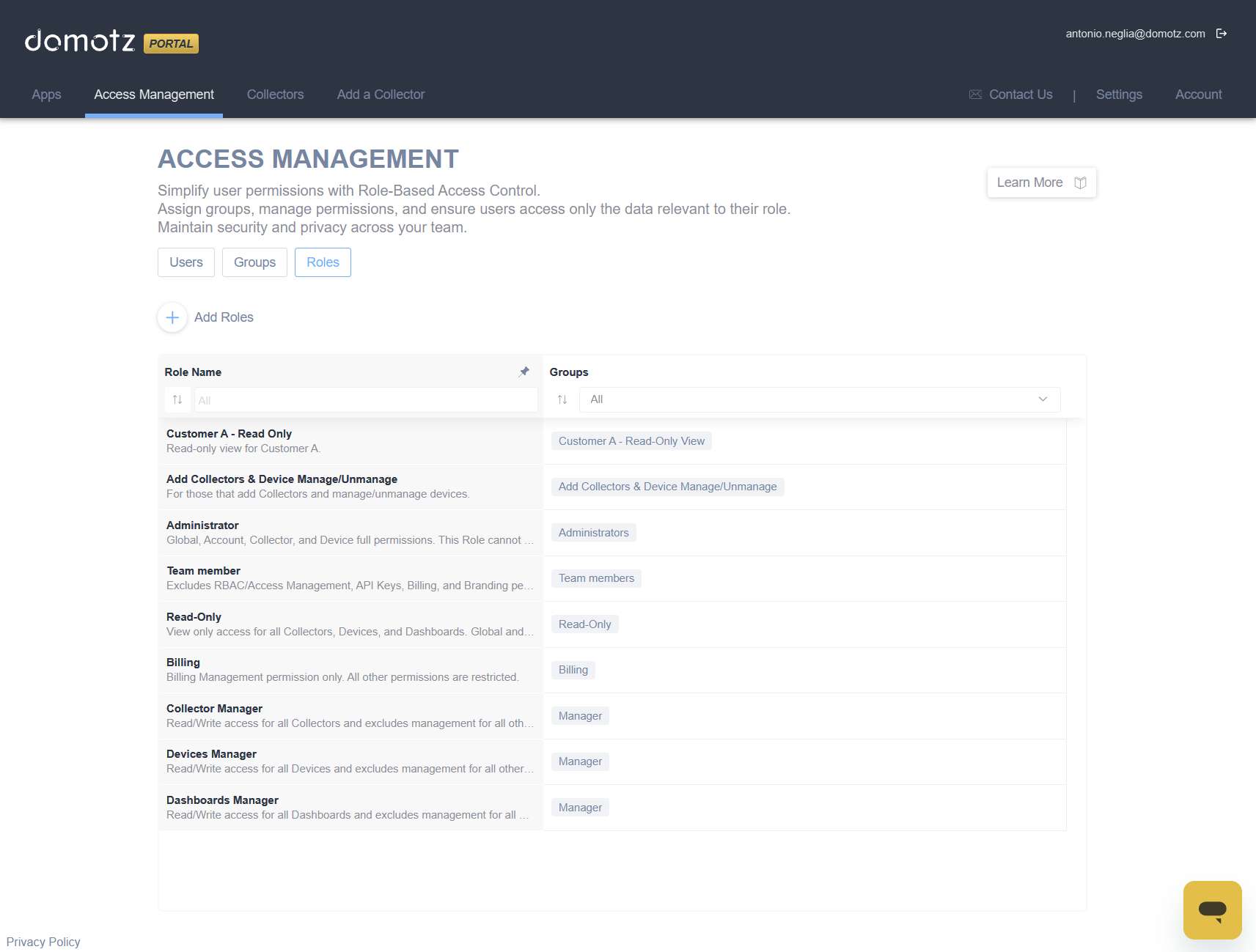
The Value of RBAC
Minimizing Operational Risk and Strengthen Your Security Posture
Limit access based on role and responsibilities to prevent accidental misconfigurations, data exposure, or unauthorized actions. Example: A support engineer can monitor device performance without the ability to reconfigure equipment.
Enabling Confident Delegation
Assign responsibilities to team members without compromising security. Example: Technicians can manage their assigned network segments without visibility into other customers’ environments.
Improving Operational Efficiency
Provision clearly defined roles to ensure users get the right access. Example: A new network operations hire is given scoped access to relevant sites.
Supporting Business and Operational Growth
As the networks you manage expand and evolve, RBAC scales with you.
Simplify Compliance
Full visibility into who can do what makes internal auditing and compliance reporting easier. RBAC ensures users have appropriate access and eliminates over-authorization.
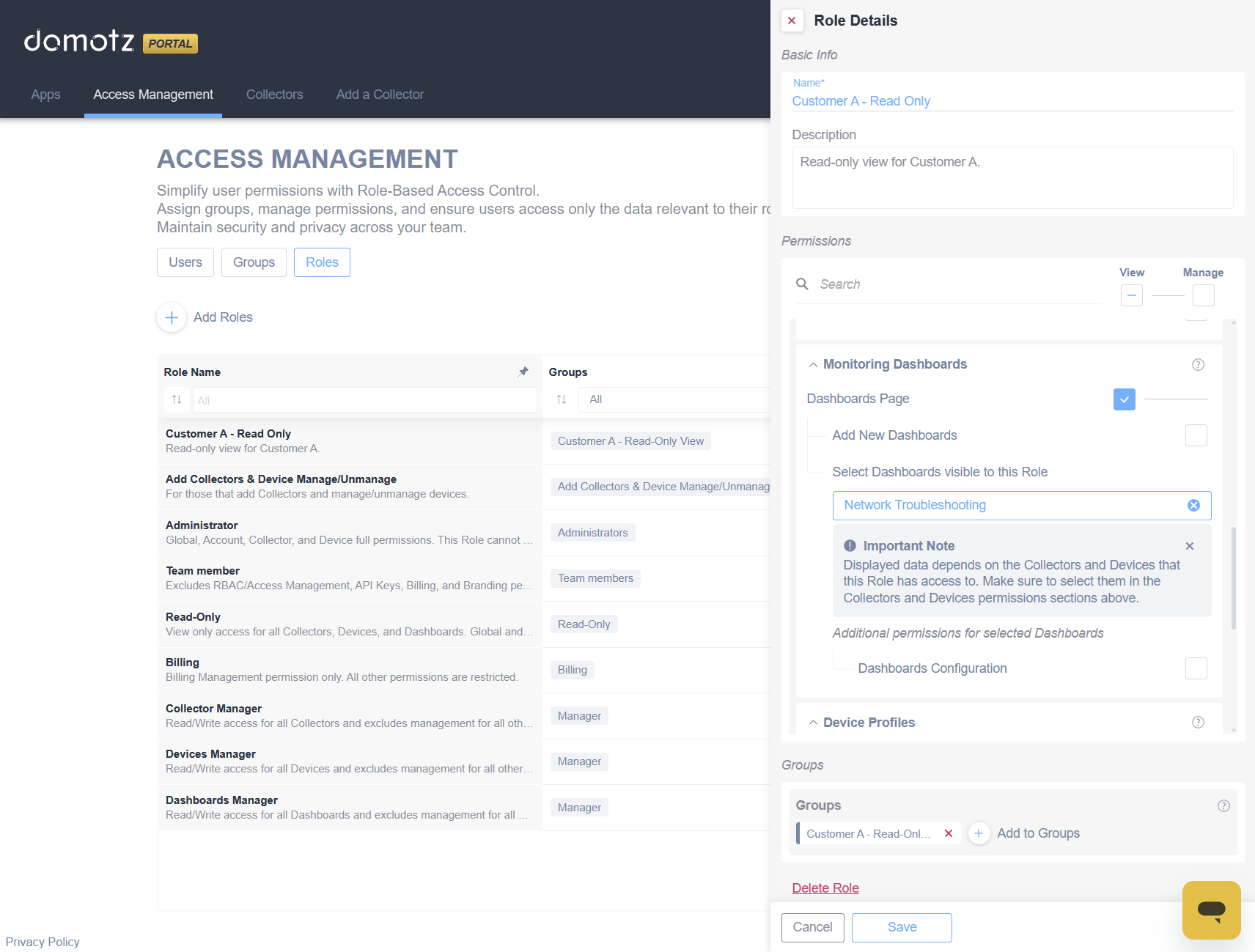
How to Get Started
Getting started is simple, and we’ve built a guided tour to walk you through the first steps.
Introducing Device Profiles
Standardize and simplify device configuration across your networks.
Every IT team knows the headaches that come with device setup. Configuring each device one by one wastes valuable time and often leads to mistakes. Without a structured approach, settings can vary wildly between sites or customers, creating confusion and troubleshooting nightmares. And as networks grow, scaling manual device configurations becomes slow, inconsistent, and risky.
We are excited to introduce Device Profiles which allow you to create standardized templates once and apply them across one or thousands of devices, eliminating repetitive work, reducing errors, and keeping every environment consistent.
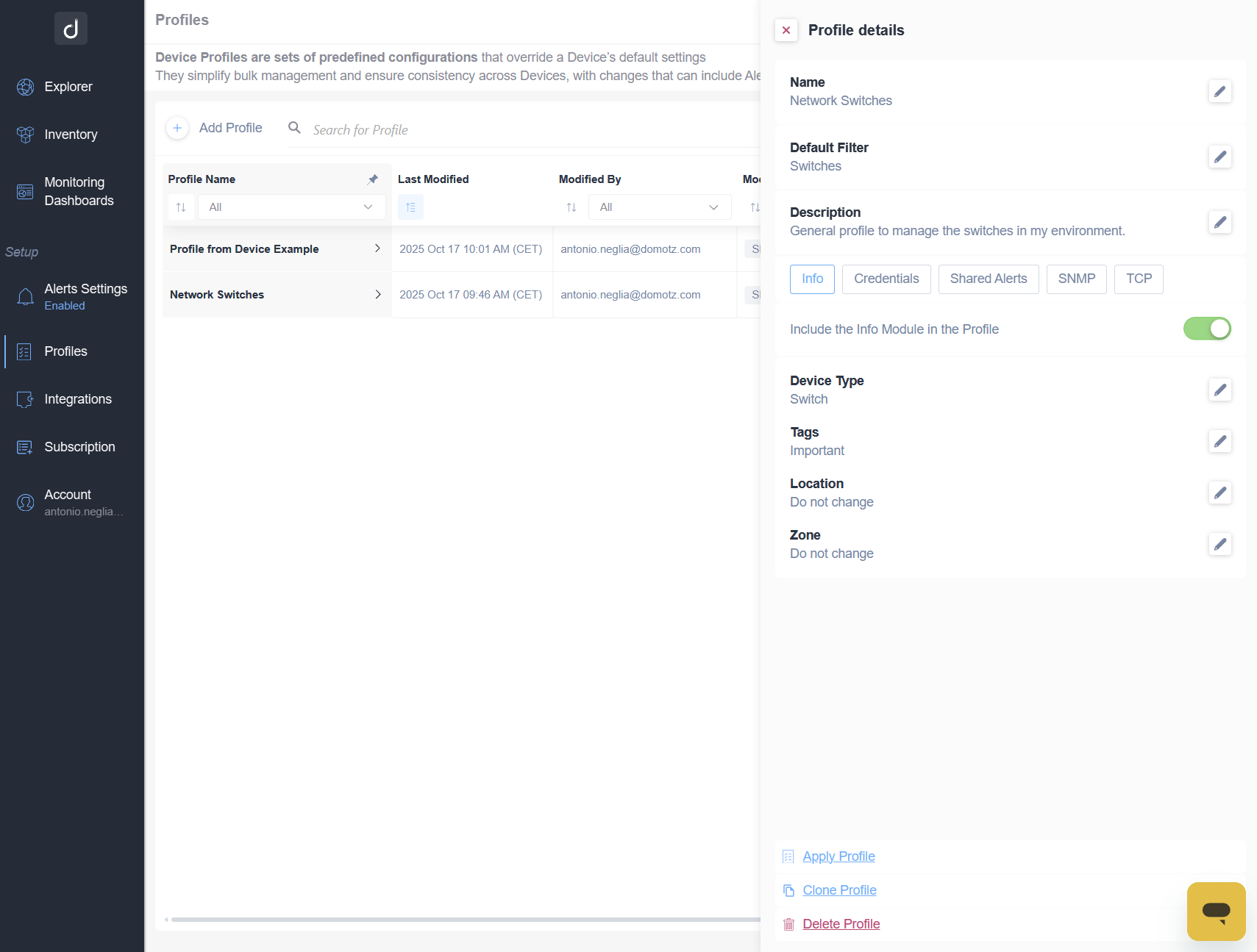
Key Features at a Glance
- Profile Management – Create, edit, clone, and assign reusable device configuration templates.
- Modular Configuration – Pick and apply only the modules you need, such as device properties, SNMP credentials, Shared Alerts, SNMP sensors, and/or TCP sensors.
- Bulk Apply Profiles – Apply profiles to single devices or large groups using static or dynamic filters.
- Automation and APIs – Apply profiles programmatically at scale via the API.
Think of these profiles as your set of “blueprints” for device configuration. They are modular, flexible, and designed to ensure that every device gets the right setup, every time.
What Problems Device Profiles Solve for You
For MSPs and IT administrators, device configuration has always been a balancing act:
- Manual Device Configuration – Configuring each device one by one wastes time and introduces errors. Device Profiles allows you to create and apply templates to devices in bulk, eliminating tedious manual configuration.
- Fragmented Approach to Monitoring – Without a structured approach, device settings can vary wildly across teams, sites, or customers. Device Profiles standardizes your device monitoring.
- Limited Visibility on Device Changes – Tracking what settings are applied, where, and by whom is nearly impossible without a centralized system. See exactly what profiles are applied to what devices and when with Device Profiles.
- Scaling the Monitoring of Devices – As the networks you oversee grow, managing device configurations manually becomes slow, inconsistent, and prone to errors. Device Profiles allows you to scale your device configuration to unlimited devices with little effort.
The Value of Device Profiles
As devices enter or change in a network, manual configuration becomes harder to manage and more prone to error. Inconsistent settings or missed updates can slow down teams, disrupt customer environments, and introduce unnecessary risk. Device Profiles eliminate these challenges by giving you a centralized way to define and apply configurations at scale, so you can manage multiple devices with confidence and consistency.
With Device Profiles, you can:
- Save time through standardization – Apply settings once and push them to as many devices as you need. You no longer need to repeat setup for every device. Create a Device Profile and roll it out across all specificized devices instantly, freeing up hours of repetitive work.
- Enforce consistency – Standardize configurations across customers, sites, and device types to reduce errors. With Device Profiles, you can save device settings as a new Profile and apply them across your network to minimize errors and deliver reliable monitoring for every device.
- Gain visibility and control – Track applied profiles, manage overrides, and see historical changes in one place.
- Support growth with confidence – As networks expand, Device Profiles help you scale and ensure every device follows your policies. Device Profiles allow you to apply existing configurations to new devices.
- Future-proof your operations – With API support and modular design, Profiles fit directly into your automation and compliance workflows.
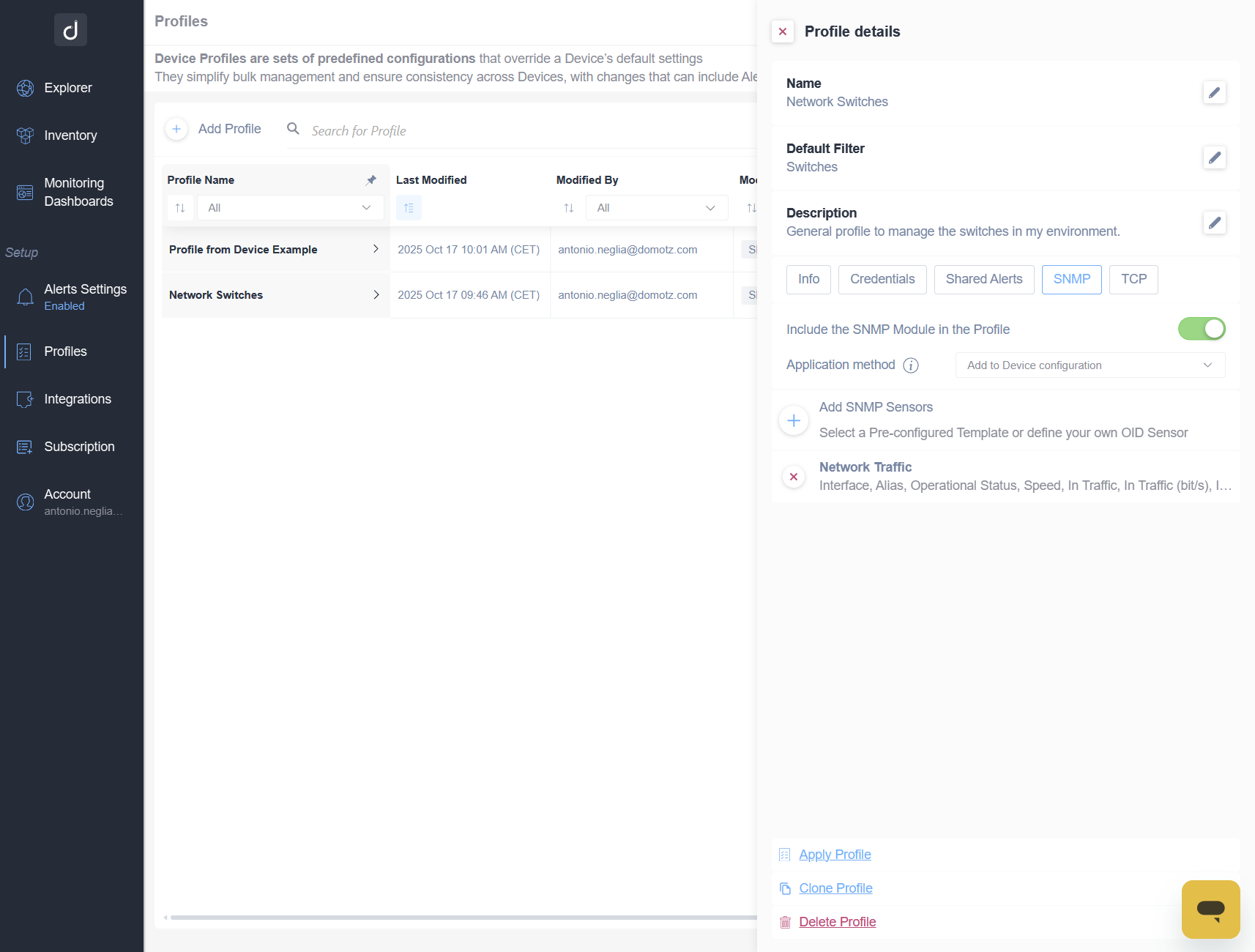
How Can I Use It?
Getting started with Device Profiles is simple, and we’ve built a guided tour to walk you through the first steps. You can also learn more about Device Profiles by visiting our knowledge base.
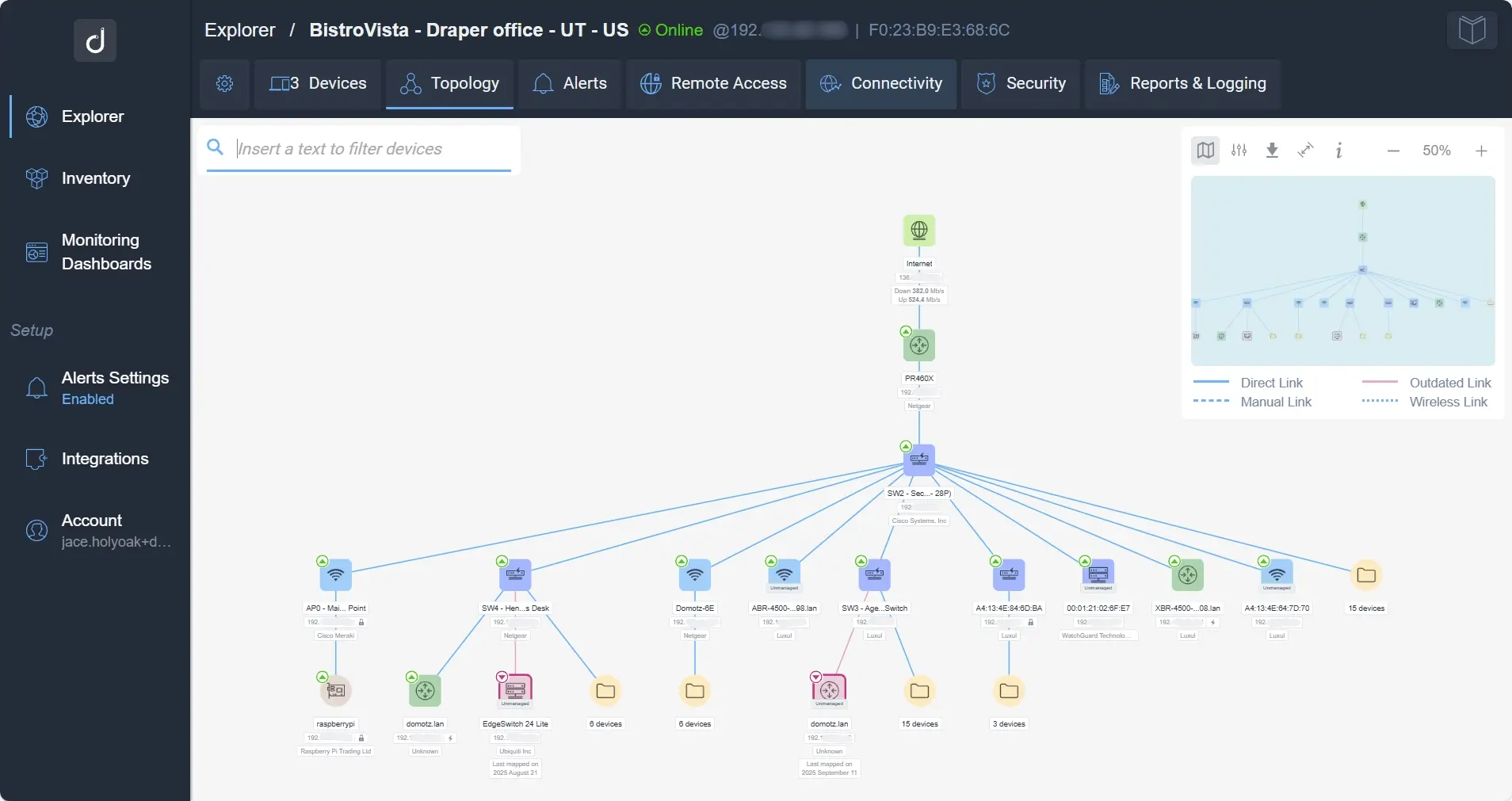
Visually Improved Network Topology
We’ve redesigned the Network Topology experience to make it easier than ever to navigate your infrastructure, spot issues, and understand device relationships at a glance.
Here’s what’s new:
- Color-Coded Devices – Quickly distinguish different device types.
- Smarter Navigation – Trace full upstream paths with clearer highlights.
- Added Indicators – Instantly see online/offline status, number of status changes, and heartbeat loss.
- Smoother Controls – Enjoy faster zooming and a cleaner layout.
- Modern Design – Better filters, legends, and panels for a simpler view.
With these updates, you get a more intuitive and visually appealing way to explore your network and device relationships.
Cut Through Ticket Noise with Alert Dependency
Tired of ticket clutter slowing down your incident management? Our new Alert Dependency feature, available through integrations with ConnectWise PSA and HaloPSA, helps you stay focused on what really matters.
Here’s how it works:
- Relationship recognition – Automatically detects the relationship of devices based on the network structure and hierarchy.
- Bundled tickets – Parent and child tickets are bundled together in ConnectWise PSA and HaloPSA.
Alert Dependency reduces ticket noise by bundling related incidents, so your team can focus on the root cause instead of sifting through duplicates. With cleaner queues and faster triage, you’ll resolve issues more efficiently and keep operations running smoothly.
To enable this feature, view the instructions below.
See What’s Possible
These new features mark a major step forward in making Domotz more accessible, safer, and scalable for the teams who depend on it every day. Ready to work faster, reduce risk, and command your networks with confidence? Start your free Domotz trial and see these new features in action.



