What does zero trust mean for your organization? Learn about the meaning, critical concepts, and implementation methods.
Zero Trust Model – Meaning, Critical Concepts, and Implementation
“When we speak about Security, we need to remember that it is not a “One-Size-Fit-All” model, but a Taylor Made one.”
Nowadays, Zero Trust, and security breaches, are fundamental concepts and words you commonly hear.
With the growing sophistication of hackers and malware and a new era of connected mobile users, billions of IoT devices, and public cloud applications everywhere, the Zero Trust model is a new reality for many organizations.
What does the Zero Trust Model mean?
But what is meant by Zero Trust?
The Zero Trust Authority Model (or Zero Trust Architecture) means there is no perimeter inside which there’s complete trust. Everything is untrusted, and a device or user only receives the least privileged access. In some cases, it requires users to authenticate multiple times, not just at the boundaries of the network.
Critical concepts of Zero Trust
The concept of “Zero Trust” has become one of the most recent trends with a new and prominent place in cybersecurity jargon.
Following the Zero Trust model, no privileged networks or locations should exist. Every device and application on any network should authenticate before establishing a connection between the client and server.
However, we shouldn’t take the concept of Zero Trust too literally.
Every computer network needs a seed of trust, such as a Kerberos server, a Certification Authority, a previously installed digital certificate, or an HSM. And this is true even in a “Zero Trust Architecture.”
What could a Zero Trust network do for your business?
Is there a chance that it is the silver bullet that will save you from ransomware, unreliable employees, or dishonest entrepreneurs? Of course, it will not.
You should view Zero trust as another layer of security you can add to your networks. It’s a layer best entrusted to a stack of other security measures, creating an observable, manageable and secure network.
Implementing a Zero Trust Architecture
Why should I implement a Zero Trust Architecture? When should I implement it?
If you are asking yourself these questions, you don’t need a Zero Trust architecture.
Every level of cybersecurity, like every physical security measure, adds costs and complexity and, in general, creates more obstacles to your company’s actual value-added processes.
Let’s just think of a workplace. You can take various measures to make it safe, such as installing alarms, purchasing a safe, or having an armed guard control the documents. Would all this be enough to achieve one hundred percent security?
Not, or maybe not, but it would increase costs disproportionately and may not solve the problem completely. The high prices can be a fundamental element in deciding which solutions to adopt and which to leave out.
Should we create a security checklist? Yes or no.
Addressing security issues is very important, but so is risk management. Instead of taking a checklist and applying it without further cost/benefit analysis to increase security, it is better to analyze the risks to which the Company is subject. Afterward, prioritize them, and deal with them in order. You may find that there are other priorities than adopting Zero Trust.
Instead of taking a checklist and applying it blindly without conducting an appropriate analysis, it is better to analyze the risks that threaten the company carefully. Then, they should be dealt with in order after setting a priority.
Following this process, you may find that there are other priorities besides adopting Zero Trust.
How to increase your business security
Increasing your business security is indeed a question with no simple answer. Here I’m going to share our version at Domotz and then explain our vision.
The security checklist is a starting point, but it must integrate within a strategy of many countermeasures. Each of them is suitable to defend against a certain number of families of attacks.
It is, therefore, a good practice to draw up a list of the possible attacks that you might incur (or ‘that pose a credible threat’) and then try to write a list of possible solutions and synergies between them. These solutions mustn’t cancel each other out.
Very often, there will not be a single tool that can protect your business, but combining more solutions will best suit the company to be the right choice.
Fundamental to this model is the periodic review. This activity allows you to review the adopted solutions, improve them, and modify them.
First steps for business security implementation
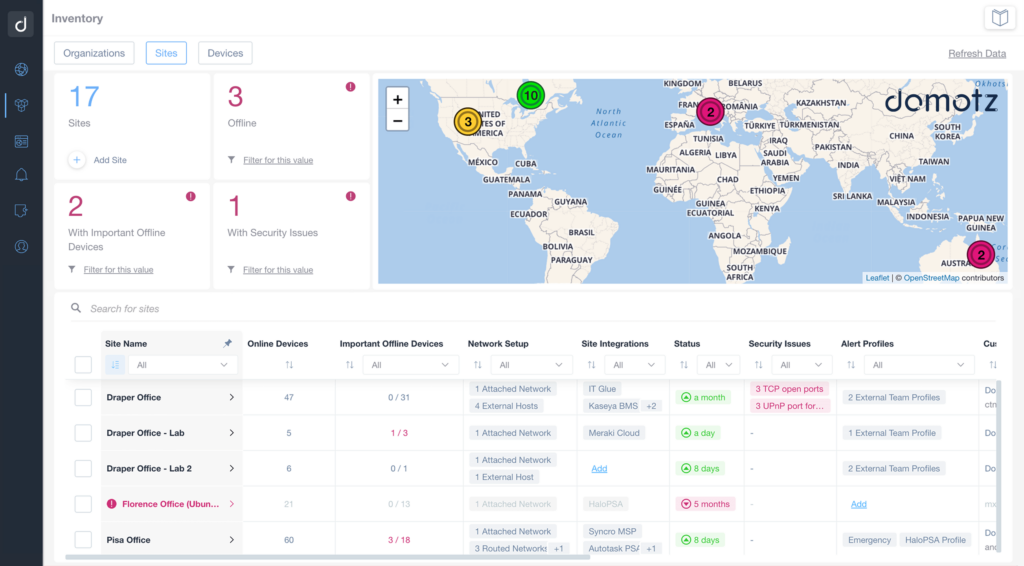
Being all tailor-made, isn’t there anything every company can do as a first step? Yes, there is a common starting point. The first thing is to know what you need to protect. So, for example, have a list of all PCs and devices that sleep connected to a network. Are there new devices that you’ve never seen before? To achieve this, you, therefore, need to have an inventory.
In this case, our network monitoring software, Domotz, can be beneficial for generating a network and device inventory for awareness of everything that is going on. Furthermore, you can use our integrations with documentation systems, such as IT Glue integration, to enter the specifics of each device to get detailed information. For instance, you could identify all your device’s licenses and when they expire.
Where should you start? What should you do?
The first step is to get an inventory of everything connected to the network. Knowing what you’re dealing with will allow you to keep it under control.
Our network monitoring and management software, Domotz, can help you with this. We do this by enumerating all PCs, checking the antivirus status, and informing you if an encrypted disk is present or not inside a device.
The latter is a significant example of “passive safety.” If you are European (or have EU-resident customers) and you lose a PC with an unencrypted hard disk, the GDPR requires you to create/open an incident. You must create an incident because the GDPR specifies you must treat all data on a lost PC as compromised.
Thanks to Domotz, you can prove that the data inside is not usable.
It is also essential to have a strong password or biometric login.
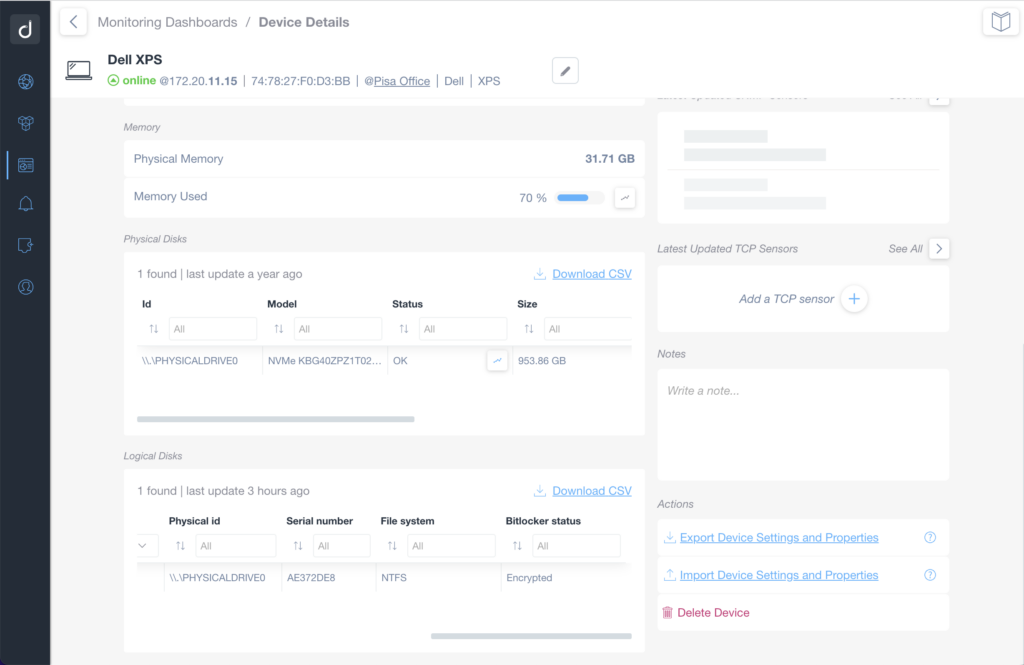
For this aspect, Domotz can therefore be used to increase security precisely because it provides you with complete visibility on your networks.
Being aware of the devices connected to the network, their brand, the model, and the essential information allows you to have important elements to make the first steps in security.



